online shopping and leisure activities.
Understanding the Importance of AI in Personalization
Artificial intelligence significantly contributes to improving customization within adaptive recommendation frameworks. By processing extensive data, AI algorithms can detect patterns and trends that guide user choices.
Artificial intelligence greatly boosts personalization in recommendation systems through data analysis to identify user preferences.
This technology enables the delivery of bespoke content, solutions, or products based on personal behavior, environment, and past interactions. Machine learning systems constantly adjust to recent developments, enhancing the relevance of recommendations over the course of time.
Moreover, AI facilitates current analysis, allowing for immediate modifications based on client engagement and outside conditions. Through these capabilities, AI transforms common offerings into customized interactions, ultimately driving client happiness and loyalty.
Consequently, organizations employing AI for personalization can successfully meet the diverse needs of their audience, nurturing deeper connections.
Keytalk's Approach to User Preferences
Keytalk implements refined algorithms to analyze patterns of user behavior, providing understandings into user preferences.
By recognizing these trends, the platform can personalize content delivery to improve user engagement.
This particular bespoke technique affirms that recommendations are relevant and timely, focusing on the personalized needs of every individual.
Understanding User Behavior Patterns
As users engage with digital platforms, their interaction patterns reveal valuable insights into likes and dislikes.
Keytalk applies sophisticated analytics to monitor user engagements, such as engagements, time invested in specific materials, and navigation paths. By analyzing these data points, Keytalk detects insights and resemblances among clients, helping to construct a detailed profile of specific preferences.
This study not only reveals trending features and subjects but also uncovers less obvious interests that could require focus. By acknowledging evolution in behavior over time, Keytalk can modify its approaches, ensuring that guidelines remain applicable and current.
In the end, understanding user behavior patterns facilitates Keytalk to enhance its approach, enhancing the overall user experience on digital platforms.
Bespoke Content Supply
For content to truly resonate with users, tailored content delivery is significantly influenced by analyzing individual preferences. Keytalk employs cutting-edge algorithms to process user data, allowing the platform to customize content in real-time. This process secures that users are provided with relevant recommendations that align with their personal interests and behaviors.
Keytalk analyzes preferences through various methods, including:
- User Interaction Records: Tracking clicks and engagement metrics.
- Demographic Data: Assessing age, region, and sex.
- Trends in Content Usage: Recognizing popular content themes.
- Feedback Collection Methods: Utilizing user ratings and reviews.
- Engagement on Social Media: Reviewing likes and shares for enhanced understanding.
Determinants of Suggestions
Comprehending the multiple components that influence recommendations is essential for enhancing the effectiveness of intelligent systems driven by AI. Multiple aspects influence the quality of recommendations, including consumer actions, preferences, and historical interactions.
Information regarding context, such as the time, setting, and device used, has a major effect on shaping personalized suggestions. Additionally, demographic information and community effects can further enhance the suggestions presented to users.
Machine learning techniques investigate these aspects to find trends and project user preferences, ensuring that the suggestions are appropriate and timely. The integration of multiple data sources ultimately enhances the overall user experience, making the recommendations specially designed and capable of meeting individual expectations.
Improving User Engagement via Personalized Suggestions
Bespoke advice can greatly enhance user engagement by delivering customized content that resonates with specific preferences.
Utilizing contextual user insights, platforms can create enhanced relevant experiences that seize attention and encourage interaction.
This method not only builds a stronger bond with users but also enhances the chances of ongoing engagement.
Bespoke Content Delivery
As individuals explore the extensive online world, bespoke content sharing emerges as an essential strategy for enhancing engagement. By tailoring suggestions based on individual preferences and behaviors, platforms can effectively increase user satisfaction and loyalty.
This process not only builds deeper connections but also enhances conversion rates.
Crucial components of customized content delivery are:
- Understanding User Behavior: Analyzing interactions to gain insights on preferences.
- Adaptive Suggestions: Issuing timely recommendations founded on present trends.
- Group Segmentation: Segmenting users by interests to better tailor content.
- Feedback Systems: Soliciting user feedback to fine-tune suggestions.
- Advanced Learning Algorithms: Applying innovative analytics to predict what users need.
These elements combine to form a more captivating and pertinent experience that connects with users.
Insights from Contextual Users
In the meantime individual choices guide content presentation, situational user knowledge enhance the personalization approach by considering the setting in which users utilize platforms.
Such insights encompass factors such as place, daily hours, type of device, and even social settings, allowing for a richer insight of user interactions. By analyzing this data, AI systems can generate personalized recommendations that resonate with users in real-time, thereby enhancing engagement.
For instance, a user browsing a travel site during their lunch break might receive proposals for travel destinations that align with their short-term planning needs.
Hence, individualized insights bridge the gap between consistent preferences and adaptive user experiences, fostering enhanced relationships and increasing the likelihood of response to advised content.
Real-World Applications of Keytalk's Technology
Keytalk's solutions has found diverse applications across various industries, transforming how businesses engage with their patrons. By leveraging context-aware recommendations, companies can enhance user engagement and drive business growth.
Noteworthy applications encompass:
- Digital Commerce: Custom shopping interactions based on user behavior and preferences.
- Travel and Leisure: Personalized travel advice and itinerary planning for individual travelers.
- Healthcare: Tailored health solutions and treatment plans based on patient data.
- Entertainment: Curated content recommendations for streaming services, improving viewer satisfaction.
- Retail: Improved shopping experiences through location-based promotions and offers.
These programs exhibit Keytalk's power to change customer interactions, making them highly pertinent and influential across different sectors.
Keytalk's creations heighten user engagement, making interactions more impactful and efficient in multiple industries.
Embracing this technology marks a change towards a more tailored business environment.
Gains from Context-Aware Advisory
Recommendations based on context give important gains by elevating user experience through personalized proposals.
They facilitate personalization on a large scale, enabling companies to address individual preferences efficiently.
Therefore, this approach contributes to boosted interaction metrics as individuals come across more suitable content and offerings.
Enhanced User Experience
As users navigate through digital platforms, the ability to receive tailored recommendations based on their unique contexts greatly enhances their overall experience.
Smart recommendations promote a seamless interaction, making sure that users access related content with ease. This brings about a more immersive and satisfying user journey.
Key benefits include:
- Improved Relevance: Recommendations match current necessities and preferences.
- Time Efficiency: Users save time searching for appropriate content.
- Better Engagement: Personalized recommendations foster deeper interactions.
- Increased Satisfaction: Users perceive a feeling of understanding and respect from the system.
- Boosted Retention: Favorable experiences inspire frequent user returns.
Personalization for Everyone
Although numerous digital platforms strive to provide personalized experiences, attaining widespread personalization remains a significant challenge.
Recommendations that are context-aware utilize artificial intelligence to analyze customer behavior, preferences, and situational factors, enabling a personalized strategy that aligns with user-specific desires. This technology facilitates the delivery of contextually appropriate content and resources, enhancing the satisfaction of users and their loyalty.
Utilizing large datasets, organizations can recognize trends that inform wise strategies and recommendations. Consequently, businesses can address diverse customer segments more effectively, leading to higher conversion rates plus customer retention.
Finally, the introduction of personalized suggestions creates a more responsive user experience, closing the divide between specific tastes and widespread use, thereby transforming how marketers reach their target audiences.
Boosted Engagement Rates
What strategies can companies effectively boost client participation in an increasingly competitive digital landscape?
Recommendations guided by context powered by intelligent systems serve as a strategic tool to enhance the user experience. By providing personalized suggestions based on user behavior and interests, businesses can foster a more engaging experience.
The gains from these recommendations consist of:
- Enhanced user contentment via targeted content delivery.
- Increased purchase rates as users identify relevant products or services.
- Boosted retention rates as individual experiences lead to ongoing visits.
- Strengthened client loyalty from favorable consumer interactions.
- Greater insights into consumer behavior, providing opportunities for refined marketing plans.
Including adaptive recommendations has the potential to revolutionize client interaction and drive business success.
Keytalk's Algorithm Uncovered
Keytalk’s approach is notable in the realm of context-aware recommendations as a result of its groundbreaking technique for incorporating user behavior and environmental factors.
Using AI-driven learning techniques, the algorithm analyzes instantaneous data, including site, hour, and user inputs, to produce tailored advice. This responsive adaptability allows Keytalk to fine-tune its analyses constantly, boosting user experience.
In addition, the algorithm makes use of collaborative filtering and content-based methods, ensuring a thorough understanding of user preferences. The result is a sophisticated system capable of delivering customized recommendations that resonate with users on various dimensions.
By integrating collaborative filtering and content-based strategies, the algorithm fosters a comprehensive understanding of user preferences for custom recommendations.
By emphasizing context, Keytalk not only enhances accuracy but also promotes deeper engagement, making it a pivotal tool in the landscape of AI-driven recommendation systems.
Future Trends in AI-Driven Personalization
The evolution of algorithms sensitive to context, for example, those utilized by Keytalk, paves the way for future trends in AI-enabled personalization.
As tech evolves, various significant trends may come into play:
- Improved User Profiling: Employing extensive insights into user habits and likes.
- Real-Time Adaptation: Models that tailor recommendations immediately according to live statistics.
- Multi-Modal Interaction: Integration of voice, text, and visual inputs for a seamless experience.
- User Privacy Oriented Techniques: Equilibrating customization with protecting user confidentiality and information security.
- Universal Synchronization: Ensuring cohesive recommendations across different devices and platforms.
These trends indicate a shift towards more intuitive and user-centric personalization, ultimately enhancing the overall user experience.
Getting Started With Keytalk's Recommendations
Exploring the effectiveness of Keytalk's suggestions involves recognizing its innovative algorithm crafted to evaluate user context efficiently. This algorithm utilizes diverse data points, including user interactions, choices, and up-to-date situations, to deliver individualized proposals.
For a successful start, users must embed Keytalk's API into their applications, facilitating smooth data transfer. Post-installation, it's important to establish user profiles and adjust settings for better recommendations. Periodically revising these profiles elevates the algorithm's correctness as time goes on.
In addition to this, using analytics tools provided by Keytalk can help track engagement and refine recommendations further. By following these steps, businesses can take advantage of the power of smart recommendations, ultimately improving user experience and driving engagement.
Keytalk's unique method defines a new standard in customized communications.
FAQ
How is User Data Privacy and Security Ensured by Keytalk?
How companies guarantee user customer data confidentiality and protection is important in today's online environment.
Keytalk utilizes advanced encryption methods to protect sensitive information and follows strict data protection regulations.
Moreover, they carry out periodic security audits and use anonymization techniques to secure user identities.
Is It Possible to Personalize My Recommendation Settings in Keytalk?
Do users have the ability to modify their experience based on their preferences? In the domain of advisory systems, tailoring is usually an essential component.
People can adjust their recommendation preferences, allowing for a more customized experience. This flexibility enables individuals to modify the types of suggestions they receive, ensuring that the content suits their interests and needs.
In the end, this level of customization enhances user satisfaction and engagement within the platform.
Can Keytalk Function on All Devices and Platforms?
That interoperability of Keytalk and a range of instruments as well as environments continues to be an necessary factor for possible users.
Overall, it is fashioned to function without issues across a broad spectrum of platforms and devices, including cell phones, tab computers, and PCs.
That said, exact compatibility may hinge on the device's specifications and the software version.
It is advised that users check the official documentation for detailed information regarding platforms that are supported to guarantee full functionality.
Frequency of Updates for Recommendations by Keytalk
A level of updates concerning suggestions fluctuates according to the designated approaches and information utilized.
Overall, systems like Keytalk aim to modify their recommendations in live time or at regular intervals to guarantee significance. This may involve continuous learning from user actions and likes.
Which Industries Stand to Benefit From Keytalk's Context-Aware Suggestions?
Several fields can greatly improve through adaptive suggestions, for instance, retail, where individualized shopping encounters increase customer satisfaction.
Medical professionals can adopt customized recommendations to enhance patient care and therapeutic alternatives.
Additionally, the hospitality industry can improve guest experiences through customized service recommendations.
Furthermore, education can make use of these insights to provide personalized learning pathways for students, making the recommendations applicable across diverse fields that stress user engagement and satisfaction.
Wrap-Up
Within the dynamic world of digital engagement, Keytalk emerges as a lighthouse, guiding users through the fog of information with adaptive suggestions. By harnessing the power of machine learning, it tailors suggestions that resonate deeply with individual preferences, much like a skilled artist who paints a unique portrait for each admirer. As the tides of customization continue to rise, Keytalk stands poised to illuminate pathways, enhancing PKI automation is essential for securing digital progress. It streamlines the management of certificates, reduces manual errors, and enhances security for digital assets. Keytalk offers creative solutions that facilitate the automation of efficient workflows and robust security protocols. By integrating these solutions, organizations can improve management, visibility, and operational efficiency. This proactive approach not only mitigates risks but also positions businesses for enduring growth. Discover how to leverage these pros further for enhanced advancement in digital transformation. While Public Key Infrastructure (PKI) might appear intricate it serves a key function in safeguarding digital communications. The PKI framework facilitates the creation, management, and distribution of cyber certificates, which authenticate the identities of users, devices, and services. PKI is primarily based on non-symmetric encryption, making use of two keys: a publicly available key and a securely kept private key. This two-key system ensures data confidentiality and integrity during transmission. PKI encompasses various components, including Certificate Authorities (CAs) responsible for issuing certificates and Registration Authorities (RAs) that confirm identities. PKI automation plays an essential role in modern digital infrastructures by streamlining certificate management processes, making it possible for organizations to smoothly cater to their cryptographic demands. This automation boosts security efforts by lessening human errors and ensuring certificates are up-to-date, hence securing sensitive information. Also, it contributes to reduced overhead expenses, allowing businesses to distribute resources optimally. Efficient certificate management is crucial for firms aiming to strengthen their digital security stance in a progressively intricate technological environment. Efficient PKI management empowers organizations to successfully handle the lifecycle of digital credentialing, diminishing risks and raising operational efficiency. Primary benefits consist of: Bolstering security strategies is vital for entities working through the complexities of digital engagements. Public Key Infrastructure automation significantly contributes to improving an organization’s security integrity. Through the automation of issuing, renewing, and revoking digital certificates, businesses can ensure that their communications and transactions remain secure. This automation lessens the risks of errors from manual input and minimizes the potential for data breaches associated with hands-on processes. As an added benefit, PKI automation enables organizations to implement more effective authentication systems, making sure that only authorized users gain access to sensitive information. As online threats become increasingly sophisticated, embracing PKI automation not only strengthens security but also fosters trust among stakeholders, paving the way for a enhanced digital landscape. Simplifying Public Key Infrastructure (PKI) not only for more information boosts security but also greatly reduces costs of operation for organizations. Through improving workflows and decreasing manual intervention, PKI automation offers several financial advantages: Integrating PKI automation enables companies to distribute resources more efficiently, thereby reducing operational costs and fostering digital expansion. Keytalk offers innovative solutions that streamline handling of digital certificates, simplifying the process for organizations to manage their digital credentials. These bolstered security frameworks significantly bolster the integrity of these systems, ensuring defense against potential threats. Moreover , efficient workflow automation optimizes processes, allowing businesses to focus on expansion and creativity. Simplified certificate handling emerges as a critical component in the domain of cybersecurity, enabling organizations to effectively manage their cryptographic assets. Keytalk offers cutting-edge solutions that streamline the challenges of managing digital certificates, facilitating business focus on expansion without risking security. Main aspects of Keytalk's streamlined certificate management are as follows: Such improvements allow for a more flexible and safe digital landscape, paving the way for boosted operational capability. Although numerous organizations strive to improve their digital defense mechanisms, putting in place solid security protocols remains a vital obstacle. Keytalk tackles this problem with advanced solutions that fortify public key infrastructure (PKI) systems. By integrating cutting-edge secure encryption methods and access control methods, Keytalk guarantees that sensitive data remains protected against advanced threats. They provide solutions that are built to accommodate changing security environments, responding to new vulnerabilities and compliance needs. Additionally, Keytalk's innovative approach includes live tracking and incident response capabilities, enabling organizations to swiftly identify and mitigate security vulnerabilities. This preemptive strategy not only safeguards digital assets but also fosters trust among stakeholders, thereby contributing to overall digital development in an increasingly interconnected landscape. Efficient workflow automation represents a transformative approach for organizations seeking to refine their operations. Keytalk’s cutting-edge solutions simplify operations, guaranteeing a hassle-free integration of Public Key Infrastructure (PKI) into daily workflows. With automation, organizations are able to attain: Such benefits empower organizations to improve productivity and emphasize strategic projects, fostering virtual development while maintaining a secure infrastructure. The solutions offered by Keytalk showcase the power of optimized workflow solutions for contemporary businesses. Controlling online certificates efficiently is vital for supporting security and trust in digital transactions. Organizations face challenges in administering a growing number of certificates across multiple environments. Enhancing the management of certificates involves implementing systematic processes that facilitate the management of issuance, renewal, and revocation. A integrated method allows for better visibility and control, reducing the risk of outdated certificates that can lead to service disruptions. Optimized certificate management boosts control and transparency, lowering the risk of lapsing certificates and preventing service outages. By categorizing certificates based on usage and importance, organizations can streamline management activities and allocate resources optimally. Merging with current IT systems boosts the full workflow, ensuring that each stakeholder is kept in the loop and aligned. Ultimately, efficient certificate handling not only fortifies security but also supports flexibility in organizations in an increasingly digital realm. An important segment of security breaches results from mistakes made by humans in certificate management procedures. Automated solutions offers a robust solution to address these threats by minimizing human intervention. With automated systems in place, organizations can effectively minimize errors and boost efficiency. The advantages of automation consist of: As organizations grow more reliant on digital resources for their operations, upgrading defensive strategies becomes paramount to protect sensitive information from evolving threats. Establishing strong security measures like encryption and multi-factor authentication reduces risks related to data breaches. Companies ought to allocate resources for constant oversight and intrusion detection systems to find flaws before they are exploited. Frequent audits and compliance inspections are necessary to guarantee that security strategies are effective against evolving threats. In addition, workforce education on security mindfulness fosters a culture of vigilance, reducing the likelihood of individual mistakes. Keytalk allows organizations to boost innovation and development by optimizing their online identity and permission management procedures. Utilizing cutting-edge technologies, Keytalk improves productivity and expedites digital change. Organizations will receive the following benefits: Because of these advantages, Keytalk positions organizations to innovate and thrive in an expanding digital arena, driving sustainable growth and business advantage. Several fields can greatly benefit from Automated PKI solutions, particularly the medical field, financial services, and tech solutions. In healthcare, it guarantees secure patient data exchanges, while the finance sector relies on it for secure transactions and compliance with regulations. The technology field applies PKI to safeguard communications and defending intellectual property. Additionally, sectors like government and telecommunications also leverage PKI automation to advance security protocols, accelerate processes, and augment overall digital trust in their operations. Keytalk integrates seamlessly with existing systems by utilizing recognized protocols and APIs, allowing for quick communication and data flow. This alignment secures that institutions can adopt Keytalk’s solutions without serious disruptions to their ongoing operations. Furthermore, its modular architecture supports adaptability, enabling businesses to alter the integration to their specific needs. Through these features, Keytalk enhances overall system capabilities while maintaining a secure environment for digital growth and identity management. Utilizing Keytalk technologies could be as detailed as constructing a multifaceted puzzle. The cost varies according to the dimensions of the organization, distinct specifications, and infrastructure compatibility. In general, firms ought to plan for expenses related to software licenses, integration support, and ongoing support. Factors such as the scale of deployment and adaptation also alter the overall investment. A thorough consultation is essential to obtain a tailored estimate that fits the organization's unique needs and goals. It is possible to automate PKI tailored to fulfill unique organizational requirements. Multiple solutions supply tailoring flexibility, permitting organizations to shape the automation process following their particular security mandates, task flows, along with compliance requirements. This adjustment may improve productivity and efficacy in managing digital certificates, ensuring that the PKI system is in harmony with the organization's operational goals. Ultimately, the versatility of automating PKI serves as an important asset for different use cases. At a moment when rotary phones are considered relics, the importance of support after the implementation phase is of utmost importance. Keytalk offers extensive assistance following the deployment of its solutions. This includes problem-solving, frequent updates, and user education to guarantee uninterrupted integration and functionality. Users reap the rewards of committed support groups prepared to tackle any challenges and boost system functionality, securing a smooth shift and ongoing success in their digital initiatives. To sum up, embracing automated PKI through Keytalk's innovative solutions not only fortifies security but also drives significant digital growth. While some may argue that automation could introduce new complexities, the streamlined certification process and reduction of manual errors ultimately create a more efficient and secure environment. By investing in advanced PKI tools, organizations can confidently navigate the digital landscape, ensuring their assets are protected while fostering innovation and growth in an increasingly competitive market.Amplify PKI Automation for Digital Progress – Secured by Keytalk
Essential Lessons
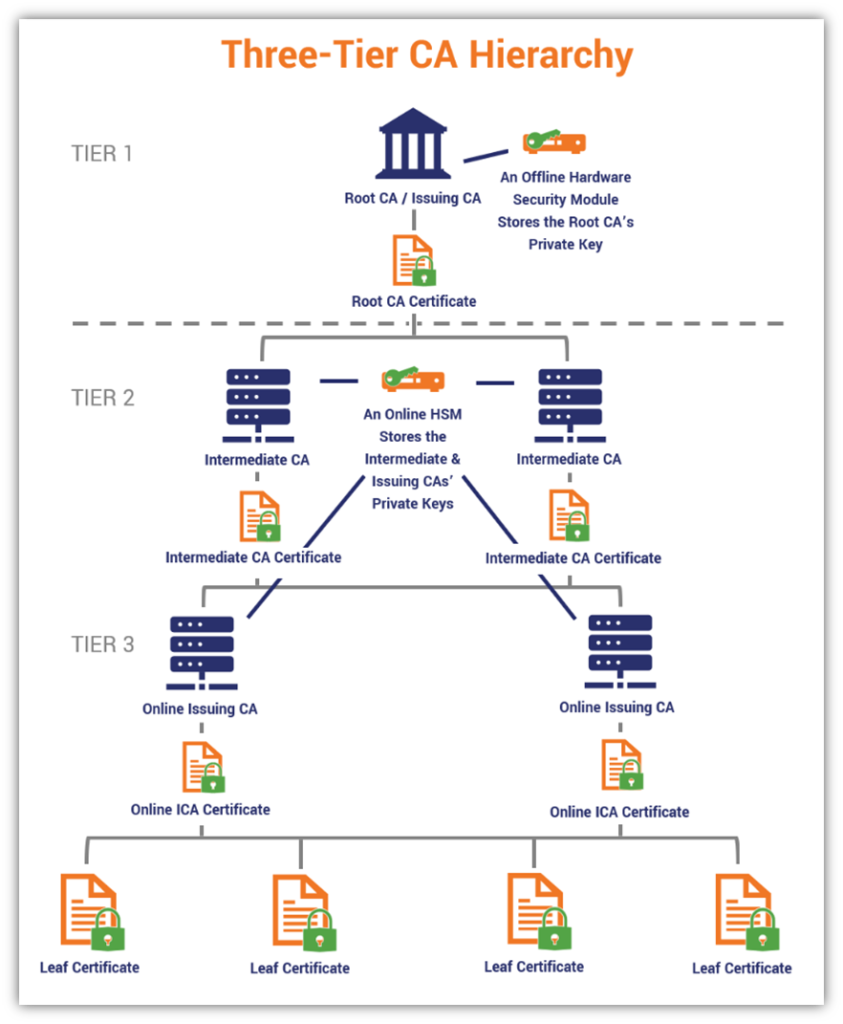
Insights into Public Key Infrastructure (PKI)
The Value of PKI Automation
Simplified Certificate Administration
Robust Security Solutions
Streamlined Operational Expenses
Keytalk's Advanced Offerings
Streamlined Certificate Management
Strengthened Security Protocols
Efficient Workflow Automation
Improving Certificate Management
Lowering Human Error Rates with Automation
Improving Protection for Digital Assets
Driving Innovation and Growth With Keytalk
FAQ
Top Industries Reaping Benefits From PKI Automation
What Is Keytalk's Integration Process With Current Systems?
What Is the Price of Keytalk Solutions Implementation?
Can We Tailor PKI Automation to Meet Specific Demands?
What Assistance Can Keytalk Provide After Implementation?
Closing Remarks